How-To: Configure the AWS cloud provider with IAM Roles for Service Accounts (IRSA)
Categories:
The AWS provider allows you to deploy and connect to AWS resources from a Radius Environment on an EKS cluster. It can be configured:
Prerequisites
- AWS account and an IAM user
- Setup AWS CLI with your AWS credentials.
- rad CLI
- Setup a supported Kubernetes cluster
- You will need the cluster’s OIDC Issuer URL. EKS Example
- Create an IAM Policy
Setup the AWS IAM Roles for Service Accounts(IRSA) for Radius
To authorize Radius to connect to AWS using AWS IAM Roles for Service Accounts(IRSA), you should assign IAM roles to Kubernetes service accounts. To associate an IAM role with a Kubernetes service account Create an IAM role and associate it with a Kubernetes service account.
- Go to Identity and Access Management (IAM) on AWS portal and create a new role.
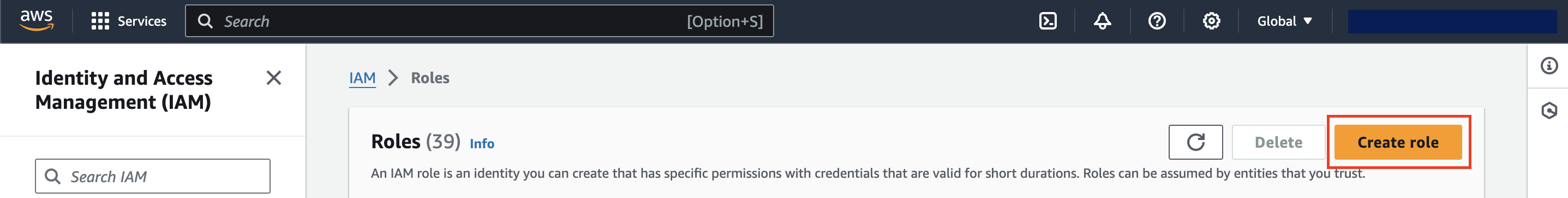
-
Select
Trusted entity typeasWeb IdentityandIdentity Provideras the cluster OIDC url.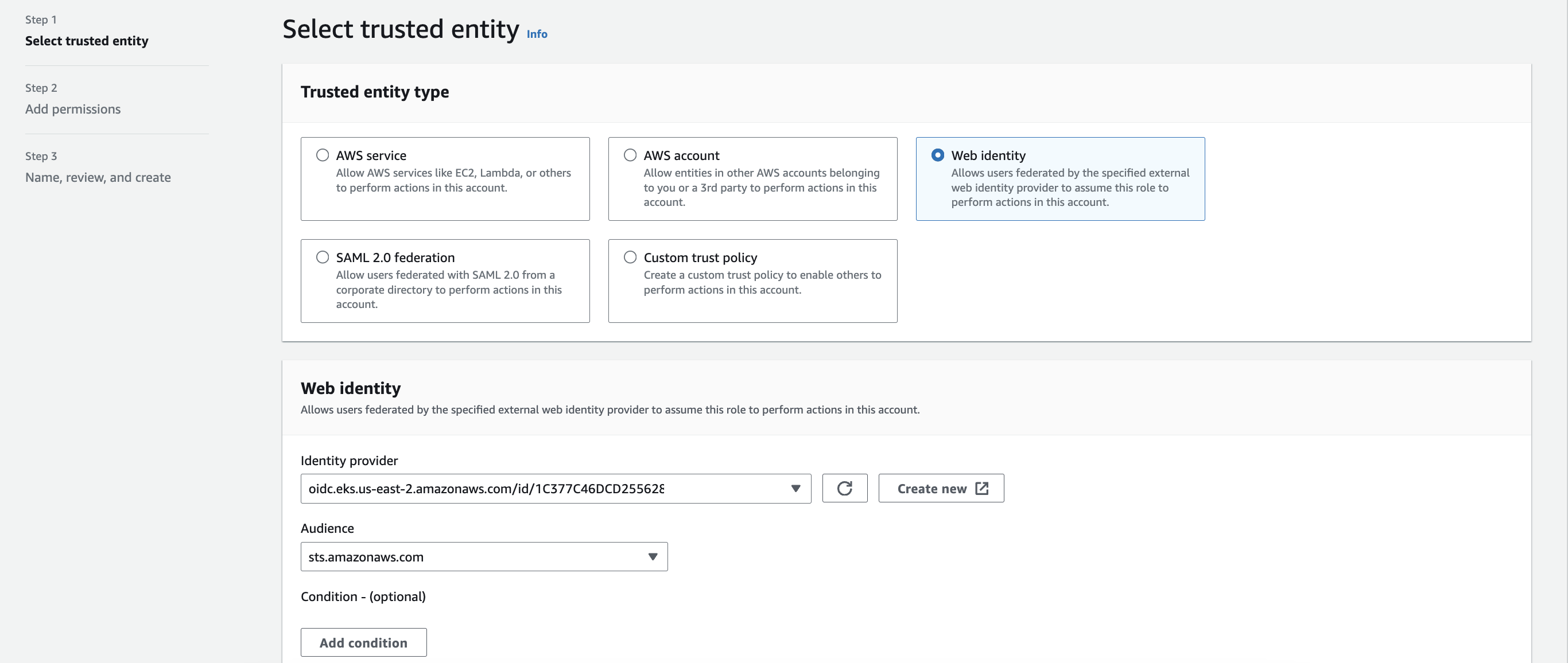
-
Select the created IAM policy to attach to your new role.
-
Add
Role Nameand create role using the default trust policy. -
Update the Trust Policy to match to the below format.
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "Federated": "arn:aws:iam::<account-id>:oidc-provider/<oidc-url>" }, "Action": "sts:AssumeRoleWithWebIdentity", "Condition": { "StringEquals": { "<oidc-url>:aud": "sts.amazonaws.com", "<oidc-url>:sub": "system:serviceaccount:radius-system:ucp" } } }, { "Sid": "Statement1", "Effect": "Allow", "Principal": { "Federated": "arn:aws:iam::<account-id>:oidc-provider/<oidc-url>" }, "Action": "sts:AssumeRoleWithWebIdentity", "Condition": { "StringEquals": { "<oidc-url>:aud": "sts.amazonaws.com", "<oidc-url>:sub": "system:serviceaccount:radius-system:applications-rp" } } } ] }
Now that the setup is complete, you can install Radius with AWS IRSA enabled.
Interactive configuration
-
Initialize a new environment with
rad init --full:rad init --full -
Follow the prompts, specifying:
- Namespace - The Kubernetes namespace where your application containers and networking resources will be deployed (different than the Radius control-plane namespace,
radius-system) - Add an AWS provider
-
Select the “IRSA” option
-
Enter IAM Role ARN.Find the ARN from the role created in the setup step.
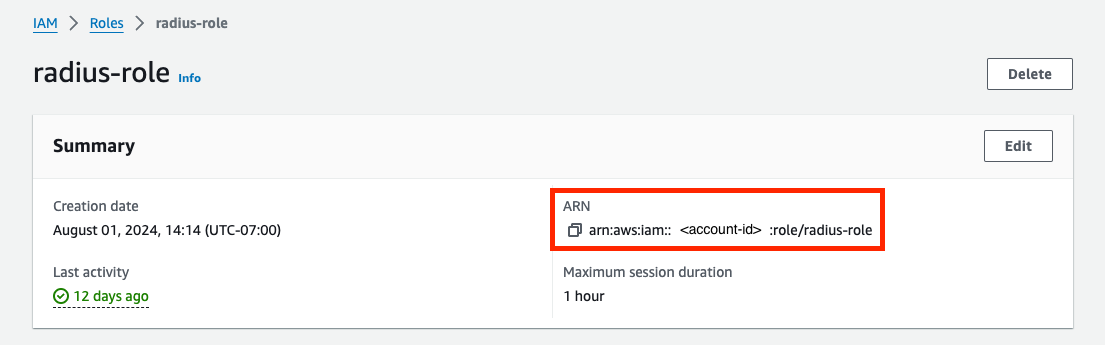
-
Confirm the AWS account ID or provide the account ID you would like to use.
-
Select a region to deploy your AWS resources to.
-
- Environment name - The name of the environment to create
You should see the following output:
Initializing Radius. This may take a minute or two... ✅ Install Radius edge - Kubernetes cluster: k3d-k3s-default - Kubernetes namespace: radius-system - AWS credential: IRSA - IAM Role ARN: arn:aws:iam::myAccountID:role/radius-role-new ✅ Create new environment default - Kubernetes namespace: default - AWS: account myAccountID and region us-east-2 ✅ Update local configuration Initialization complete! Have a RAD time 😎 - Namespace - The Kubernetes namespace where your application containers and networking resources will be deployed (different than the Radius control-plane namespace,
Manual configuration
-
Use
rad install kubernetesto install Radius with AWS AWS IAM Roles for Service Accounts(IRSA) enabled:rad install kubernetes --set global.aws.irsa.enabled=true -
Create your resource group and environment:
rad group create default rad env create default -
Use
rad env updateto update your Radius Environment with your your AWS region and AWS account ID:rad env update myEnvironment --aws-region myAwsRegion --aws-account-id myAwsAccountId -
Use
rad credential register aws irsato add the AWS IRSA credentials:rad credential register aws irsa --iam-role myRoleARNRadius will use the provided roleARN for all interactions with AWS, including Bicep and Recipe deployments.
Feedback
Was this page helpful?
Glad to hear it! Please feel free to star our repo and join our Discord server to stay up to date with the project.
Sorry to hear that. If you would like to also contribute a suggestion visit and tell us how we can improve.